Internet access required for CPM operations
CPM Server:
All outbound CPM communication is to the 443 port (https)
For ongoing operations for a production CPM server it needs to access AWS endpoints to use AWS APIs.
You can decide to expose only relevant regions.
AWS endpoint information can be found here:
http://docs.aws.amazon.com/general/latest/gr/rande.html
You should keep the EC2, EBS, RDS, VPC, KMS, IAM, STS, SNS & Redshift services available.
During the trial and an initial registration of the purchased instance, CPM needs to access our licensing service to get the license, so you need to keep port 443 open from the CPM instance to the Internet.
After you have purchased a non-BYOL edition and registered your CPM instance, you may delete this rule, leaving only communications to the AWS endpoints.
BYOL edition requires to keep port 443 open from the CPM instance to the Internet after the purchase.
Troubleshooting CPM Server's connectivity:
If CPM has a problem accessing specific endpoints, try using them instead of "aws.amazon.com".
CPM Agent:
CPM Agent needs to be able to connect to the CPM Server over port 443.
To verify that it can do that, you can open CPM's GUI in a browser on the Agent's instance.
If the browser can connect, so can the Agent.
All outbound CPM communication is to the 443 port (https)
For ongoing operations for a production CPM server it needs to access AWS endpoints to use AWS APIs.
You can decide to expose only relevant regions.
AWS endpoint information can be found here:
http://docs.aws.amazon.com/general/latest/gr/rande.html
You should keep the EC2, EBS, RDS, VPC, KMS, IAM, STS, SNS & Redshift services available.
During the trial and an initial registration of the purchased instance, CPM needs to access our licensing service to get the license, so you need to keep port 443 open from the CPM instance to the Internet.
After you have purchased a non-BYOL edition and registered your CPM instance, you may delete this rule, leaving only communications to the AWS endpoints.
BYOL edition requires to keep port 443 open from the CPM instance to the Internet after the purchase.
CPM v2.3 and newer has NTP daemon installed (please upgrade if you are using an older version).
In order for NTP to function, you must enable in your firewall full unrestricted access to UDP port 123 in both directions between the CPM instance and Amazon's NTP servers:
server0.amazon.pool.ntp.org
server1.amazon.pool.ntp.org
server 2.amazon.pool.ntp.org
server 3.amazon.pool.ntp.org
If CPM's time will go out of sync with AWS, it won't be able to perform any backups, or send notifications about failures.
In order for NTP to function, you must enable in your firewall full unrestricted access to UDP port 123 in both directions between the CPM instance and Amazon's NTP servers:
server0.amazon.pool.ntp.org
server1.amazon.pool.ntp.org
server 2.amazon.pool.ntp.org
server 3.amazon.pool.ntp.org
If CPM's time will go out of sync with AWS, it won't be able to perform any backups, or send notifications about failures.
Troubleshooting CPM Server's connectivity:
To test connectivity outside of the CPM application itself, please
connect to the instance using SSH (username: cpmuser and your assigned
private key) and try this command:
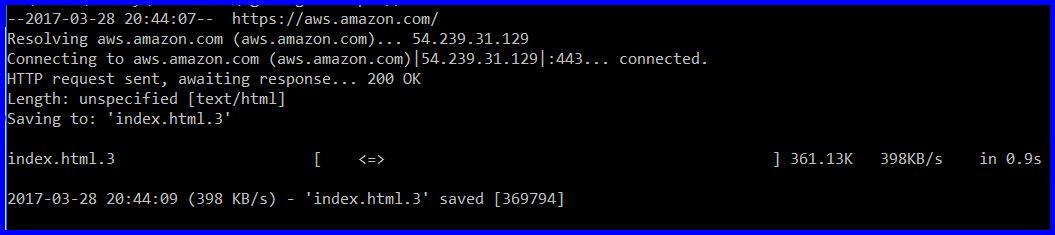
See what it returns - there must be a failure with either resolving the URL or connecting to it.
If you don't see HTTP response 200 "OK" like in the
screenshot below, there is a problem with either DNS resolution or a
proxy refusing connections.
CPM Agent:
CPM Agent needs to be able to connect to the CPM Server over port 443.
To verify that it can do that, you can open CPM's GUI in a browser on the Agent's instance.
If the browser can connect, so can the Agent.
File Level Restore Workers:
File Level Restore Worker needs to be able to connect to the CPM Server over ports 443 and 22.
File Level Restore Worker needs to be able to connect to the CPM Server over ports 443 and 22.
You can test connectivity from the Worker by connecting to the worker over SSH and running these commands:
For port 22: ssh cpmserveripaddress
The result should be "cpmuser@cpmserveripaddress: Permission denied (publickey)."
If connection is blocked, you will receive (after a delay) "ssh: connect to host cpmserveripaddress port 22: Connection timed out"
For port 443: wget --no-check-certificate https://cpmserveripaddress/
This command should result in status 302 (redirecting to "/signin/") followed by status 200
Important: In order to be able to login to the worker
instance over SSH (using "ubuntu" username) you have to make sure that
you have configured the workers to use a key pair:
**If CPM is using http proxy, you need to make sure that it is configured to pass ssh communication also
S3 Workers:
S3 worker needs the same access as File Level Restore Worker, plus access to the AWS S3 public gateway IPs, same region as the S3 bucket
S3 worker needs the same access as File Level Restore Worker, plus access to the AWS S3 public gateway IPs, same region as the S3 bucket
If using an ACL, please make sure the proper ports are open for bi-directional communication between the worker and S3: https://aws.amazon.com/premiumsupport/knowledge-center/connect-s3-vpc-endpoint/
The worker will connect to S3 via internet, even if the CPM server and S3 bucket are in the same region.
The worker must have a public IP assigned by the subnet; -or- the subnet must be configured with a NAT gateway, for the worker to communicate with S3.
Only if the EBS backups and S3 bucket are in the same region, this can be worked around by configuring an S3 endpoint as shown here: https://n2ws.com/support/documentation/appendix-s3-configuration
The worker must be able to resolve the DNS name of the region with your S3 bucket. (e.g. https://s3.us-west-2.amazonaws.com/). Please ensure the worker will be able to resolve DNS names of S3 endpoints.
If an HTTP proxy is necessary to access public IPs, ensure this is properly configured in the worker settings and not blocking the transfer to s3. It may be advisable to test by opening internet to the worker without a proxy in some cases to be sure the proxy is not causing an issue.
The worker will connect to S3 via internet, even if the CPM server and S3 bucket are in the same region.
The worker must have a public IP assigned by the subnet; -or- the subnet must be configured with a NAT gateway, for the worker to communicate with S3.
Only if the EBS backups and S3 bucket are in the same region, this can be worked around by configuring an S3 endpoint as shown here: https://n2ws.com/support/documentation/appendix-s3-configuration
The worker must be able to resolve the DNS name of the region with your S3 bucket. (e.g. https://s3.us-west-2.amazonaws.com/). Please ensure the worker will be able to resolve DNS names of S3 endpoints.
If an HTTP proxy is necessary to access public IPs, ensure this is properly configured in the worker settings and not blocking the transfer to s3. It may be advisable to test by opening internet to the worker without a proxy in some cases to be sure the proxy is not causing an issue.
Version 3.1:
in version 3.1 we started using EBS direct API for S3 operation, this API enable lets us read the blocks from the snapshots.
in version 3.1 we started using EBS direct API for S3 operation, this API enable lets us read the blocks from the snapshots.
This means that in addition to the above, you also need to make sure that communication is opened to the relevant EBS endpoints:
If your worker is in a private VPC, then you need to enable communication to this endpoint via your proxy or using VPC endpoints
Related Articles
CPM may malfunction if security group is misconfigured
CPM may malfunction if security group is misconfigured. For example CPM may experience slow response and timeout in CPM console/GUI when adding backup targets: ERROR: policy_add_databases(.\cpmserver\cpm\views.py:3415) rds.RDSConnection or ...How to create and configure an EBS Endpoint for CPM Workers
This article will provide step-by-step instructions on how to create and configure an EBS Endpoint for CPM workers (v3.1 and up) Step 1: Let's say that you have created this VPC for your workers: In this example, we allocated IPv4 addresses ...S3Sync: Source bucket: prod_bucket_A to Destination bucket: prod_bucket_B failed fatal error:S3SYNC An error occurred (AccessDenied) when calling the ListObjectsV2 operation: Access Denied
Issue: When trying to synchronize two buckets in CPM I get the following error message. S3Sync: Source bucket: Prod_bucket to Destination bucket: Dev_bucket failed fatal error: S3SYNC An error occurred (AccessDenied) when calling the ListObjectsV2 ...Troubleshooting File Level Recovery (FLR) communication issue
CPM Configuration File-level recovery requires N2WS to recover volumes in the background and attach them to a temporary EC2 ‘worker’ launched for the operation, The worker will be launched in the same account and region as the snapshots being ...CPM may fail to communicate with AWS gateways with the "timed out" error
CPM may fail to communicate with AWS gateways with the "timed out" error during various operations: ERROR: run_snapshots(.\cpmagent\agent.py:1462) snapshot of policy PolicyName, volume: vol-0123456789abcdef failed (independent). Reason: timed out ...