Knowledge Base Article: Resolving Access Denied Error in N2WS S3 Sync
Issue
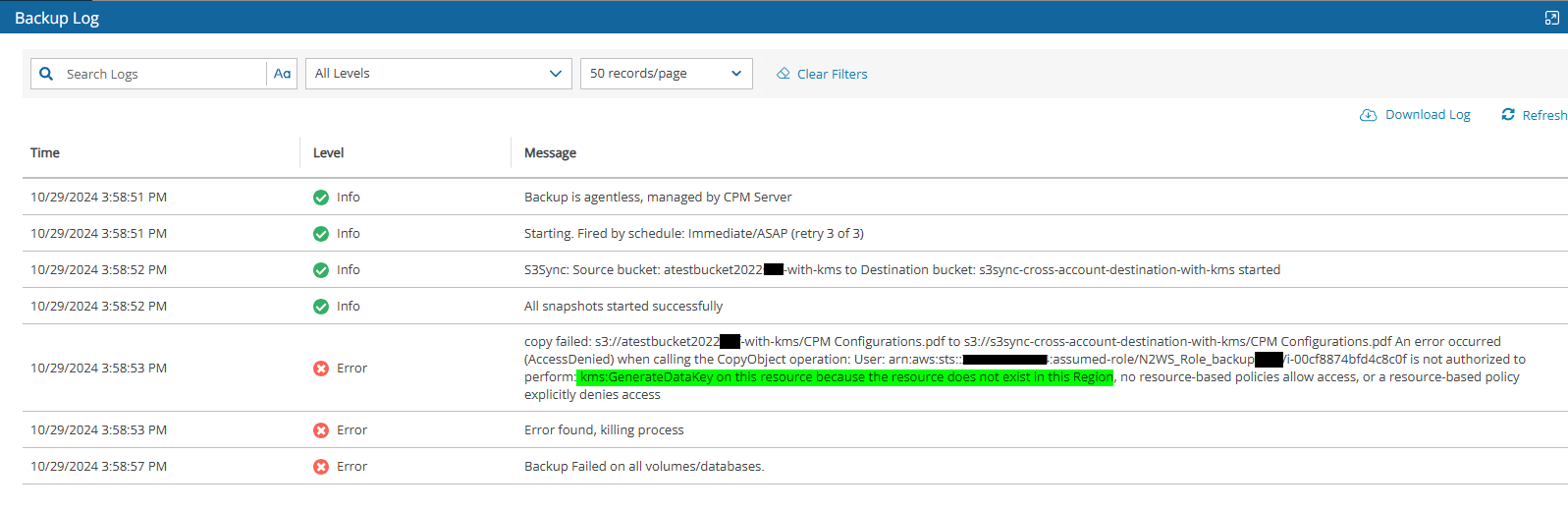
When attempting to copy an object between S3 buckets using AWS KMS for encryption, you encounter the following error:
copy failed: s3://atestbucket2022-with-kms/CPM Configurations.pdf to s3://s3sync-cross-account-destination-with-kms/CPM Configurations.pdf An error occurred (AccessDenied) when calling the CopyObject operation: User: arn:aws:sts::123456789123:assumed-role/N2WS_Role_backup/i-00cf8874bfd4c8c0f is not authorized to perform: kms:GenerateDataKey on this resource because the resource does not exist in this Region, no resource-based policies allow access, or a resource-based policy explicitly denies access
Cause
This error occurs because the user or role performing the copy operation does not have the necessary permissions to use the kms:GenerateDataKey action on the specified KMS key. This can happen if the KMS key is not accessible from the target account or if the key is not available in the specified region.
Solution
To resolve this issue, you need to allow access from the target account to the KMS key in the source account. Follow these steps:
Modify the KMS Key Policy:
- In the AWS Management Console, navigate to the KMS service.
- Select the customer managed key used for encryption.
- Under the Key Policy section, add a statement to allow access from the target account.
Example policy statement:
{ "Version": "2012-10-17", "Id": "key-policy", "Statement": [ { "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::123456789123:role/N2WS_Role_backup" }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }, { "Sid": "Allow cross-account access", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::target-account-id:root" }, "Action": [ "kms:GenerateDataKey", "kms:Decrypt" ], "Resource": "*" } ] }Add the Source Account Under Other AWS Accounts:
- In the KMS console, go to the Customer managed keys section.
- Select the relevant key and navigate to the Other AWS accounts tab.
- Add the source account ID to allow cross-account access.
Verify IAM Role Permissions:
- Ensure the IAM role
N2WS_Role_backuphas the necessary permissions to perform thekms:GenerateDataKeyaction. - Example IAM policy:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "kms:GenerateDataKey", "kms:Decrypt" ], "Resource": "arn:aws:kms:region:account-id:key/key-id" } ] }
- Ensure the IAM role
Check Region Configuration:
- Ensure the KMS key exists in the same region as the S3 buckets involved in the copy operation.
Test the Configuration:
- After updating the policies, test the copy operation to ensure it completes successfully.
By following these steps, you should be able to resolve the AccessDenied (kms:GenerateDataKey) error and successfully copy objects between S3 buckets using AWS KMS for encryption.
Related Articles
S3Sync: Source bucket: prod_bucket_A to Destination bucket: prod_bucket_B failed fatal error:S3SYNC An error occurred (AccessDenied) when calling the ListObjectsV2 operation: Access Denied
Issue: When trying to synchronize two buckets in CPM I get the following error message. S3Sync: Source bucket: Prod_bucket to Destination bucket: Dev_bucket failed fatal error: S3SYNC An error occurred (AccessDenied) when calling the ListObjectsV2 ...Resolving Access Denied Errors in N2WS S3 Sync (CopyObject or ListObjectsV2 )
When using N2WS S3 sync policies, you might encounter the following errors: CopyObject Operation Error: 10/29/2024 03:02:11 PM, Error, "copy failed: s3://atestbucket2022saif/cli commands.txt to s3://s3sync-cross-account-destination/cli commands.txt ...S3 Sync cross account failing due to AccessDenied error
Issue: When doing cross account S3 sync, it fails due to missing permissions on the bucket copy failed: s3://mybucketname//file_name.txt to s3://other_bcuket//file_name.txt An error occurred (AccessDenied) when calling the CopyObject operation: ...How to use AWS IAM Policy Simulator to troubleshoot N2WS Backup permission issues.
Background: Permission issues are one of the most common errors seen by users of N2WS Backup and this article explains how you can use the IAM Policy Simulator to help you narrow down whether permissions are allowed by an IAM User or a Role. This ...Internet access required for CPM operations
CPM Server: All outbound CPM communication is to the 443 port (https) For ongoing operations for a production CPM server it needs to access AWS endpoints to use AWS APIs. You can decide to expose only relevant regions. AWS endpoint information can be ...